
How data governance regulations and standards shape DocuSign's rigorous security and privacy practices

Emerging Data Protection Schemes The Ultimate Step-By-Step Guide by Gerardus Blokdyk - Ebook | Scribd

Cloud Data Protection Powerpoint Presentation Slides | Presentation Graphics | Presentation PowerPoint Example | Slide Templates



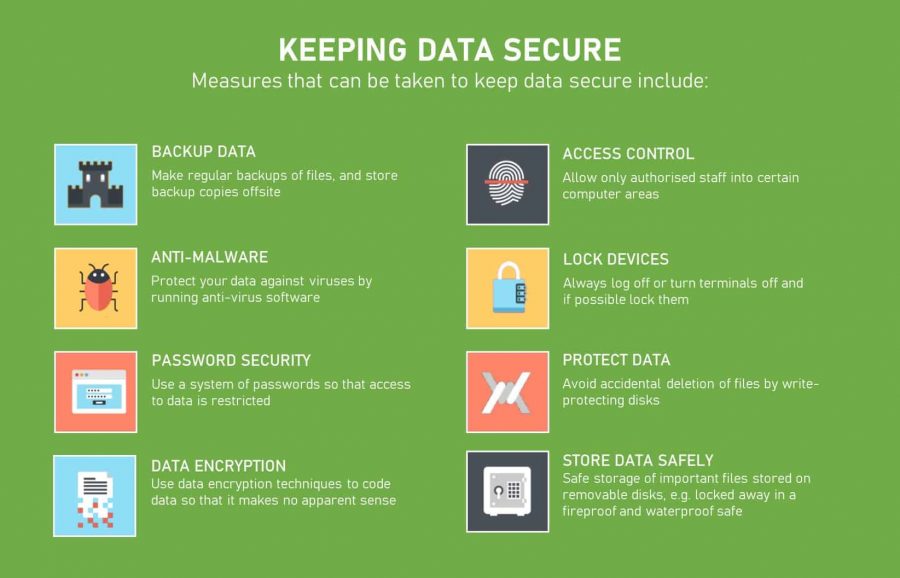


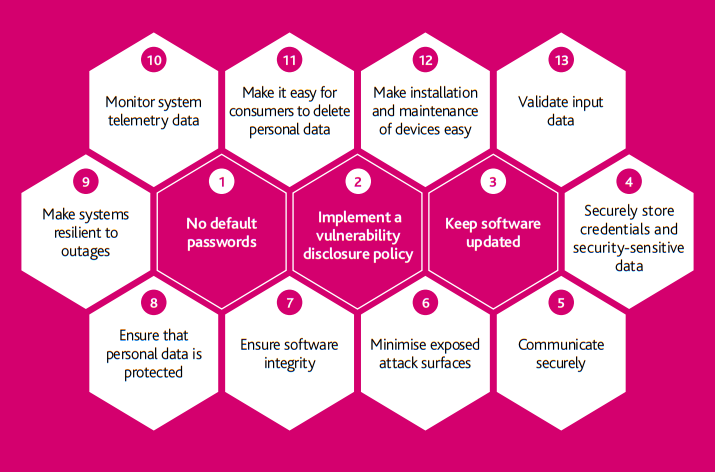



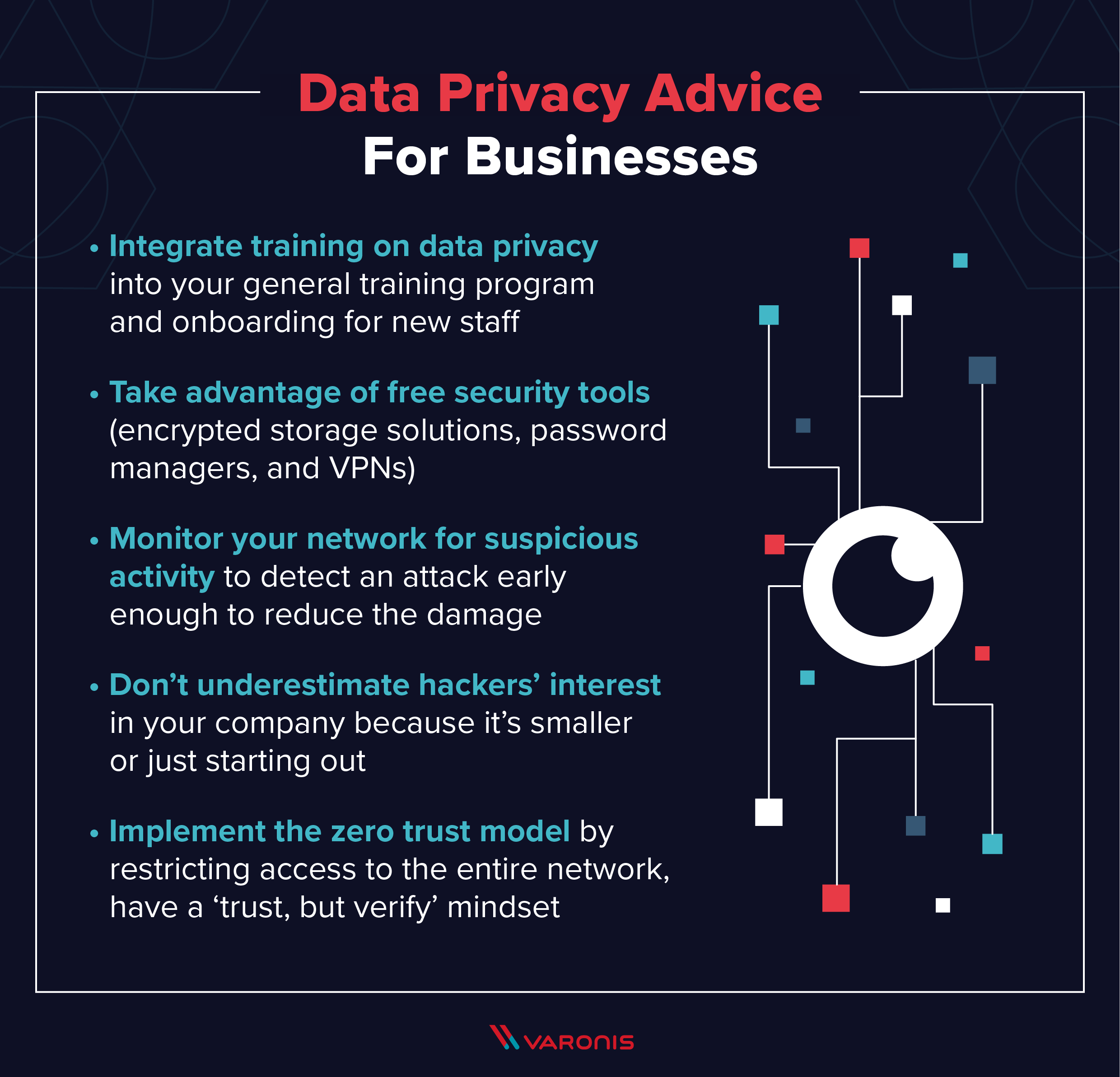

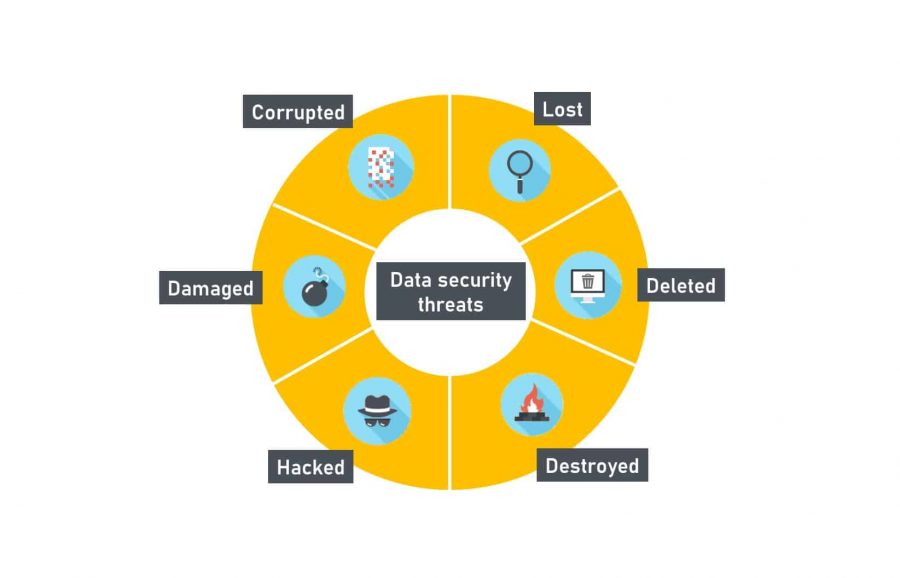
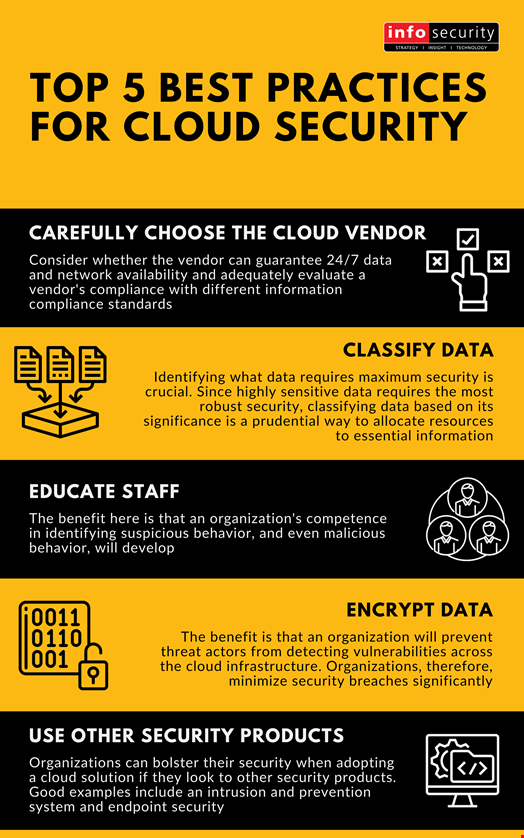



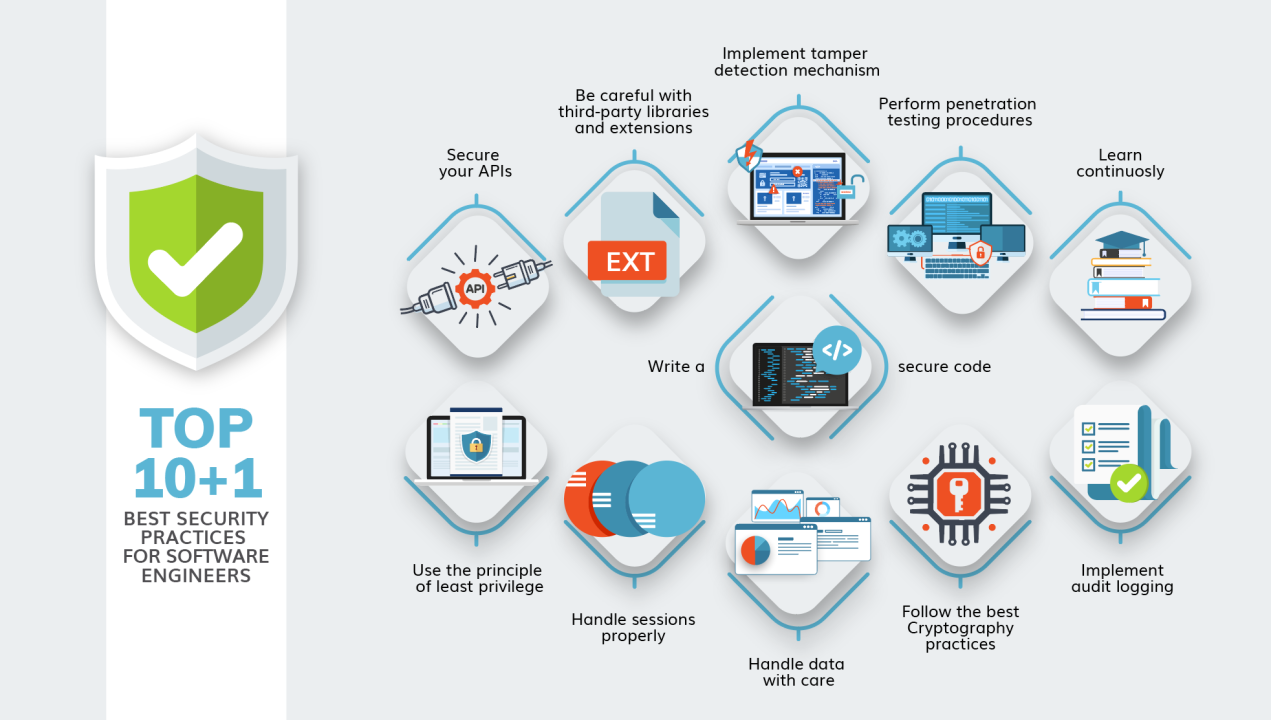
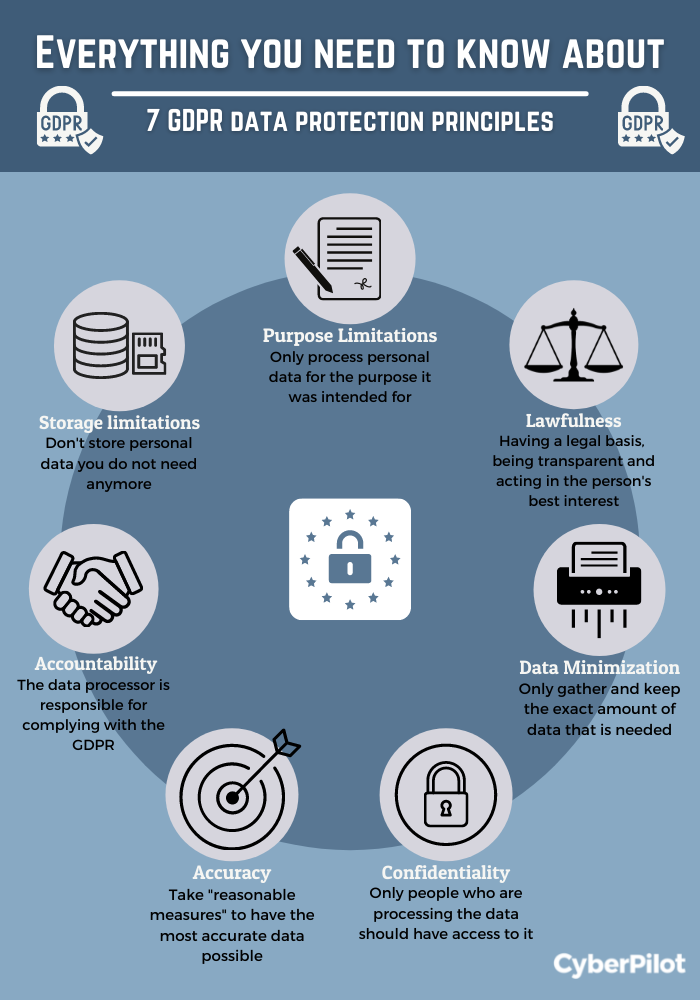

![22 Best Practices for Protecting Data Privacy in 2023 [Infographic] - TitanFile 22 Best Practices for Protecting Data Privacy in 2023 [Infographic] - TitanFile](https://www.titanfile.com/wp-content/uploads/2022/08/22-Best-Practices-for-Protecting-Data-Privacy-in-2022.png)
