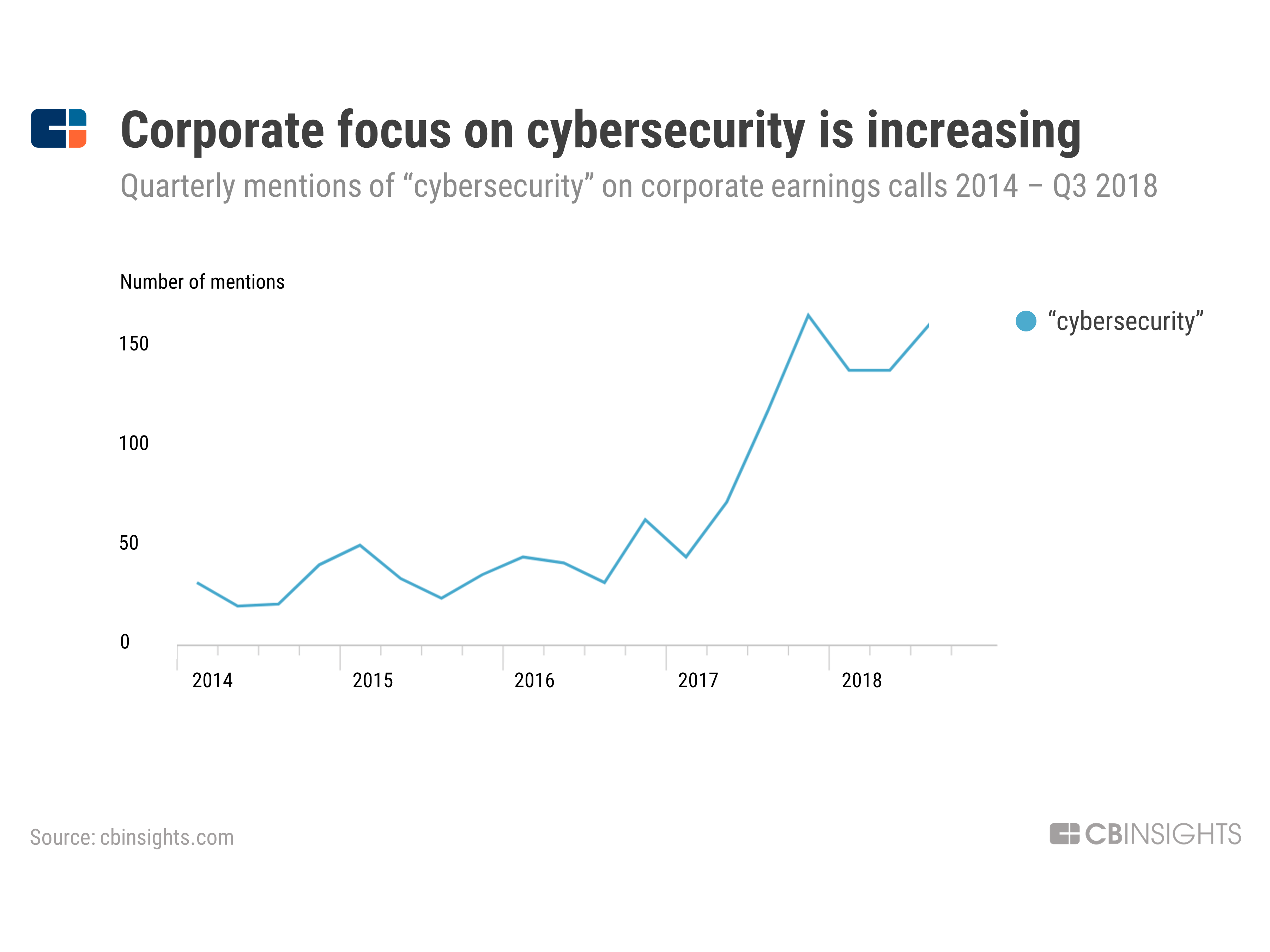
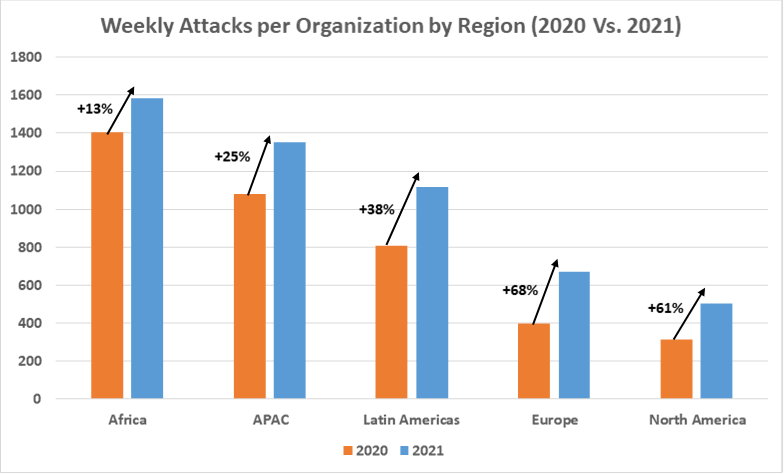
Nearly 65% of Affected Public Companies Did Not Report Cybersecurity Breaches to the SEC | Nearly 65% of Affected Public Companies Did Not Report Cybersecurity Breaches to the SEC - Audit AnalyticsAudit Analytics

Are You Spending Too Much (or Too Little) on Cybersecurity? | Data Center Knowledge | News and analysis for the data center industry

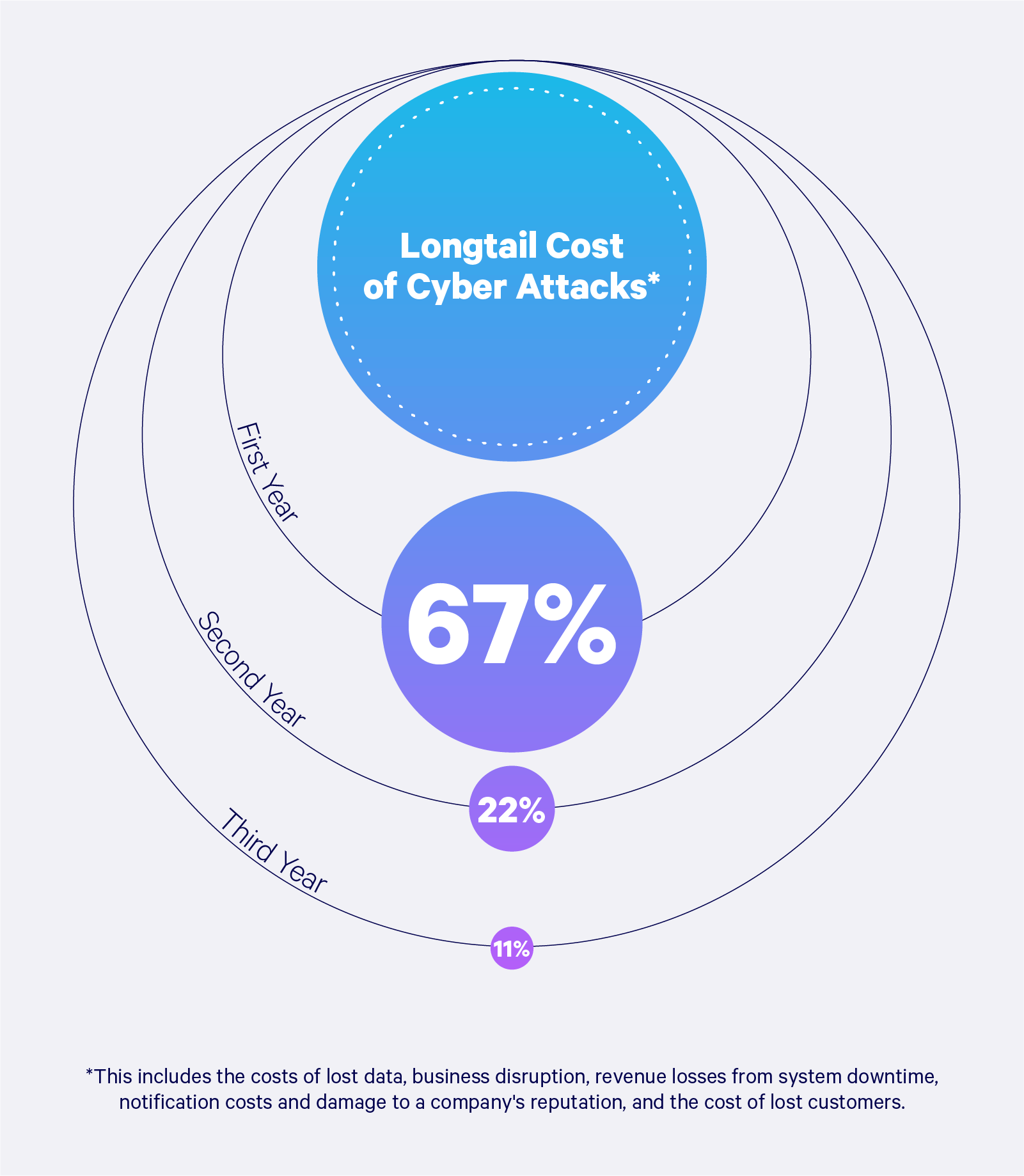

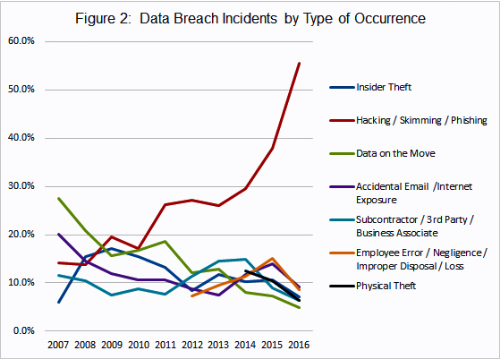








![10 Cybersecurity Statistics in 2019 [Infographic] - TitanFile 10 Cybersecurity Statistics in 2019 [Infographic] - TitanFile](https://www.titanfile.com/wp-content/uploads/2019/05/Cybersecurity-Statistics-2019-Infographic-2.png)